How We Built the First Cybergovernance Platform

The Opportunity and the Team
In December 2014, my former CEO Mike Shultz called about a developing opportunity. The SEC was holding corporate directors personally liable for cybersecurity breaches if they hadn’t exercised “prudent business oversight” beforehand. Mike wondered if we could combine a software platform with litigation insurance to protect the directors. Since together we had crafted a successful exit strategy that led to Infoglide Software’s 2013 acquisition by FICO, I suggested, “Let’s partner on this one!”
Charlie Leonard, Bob Barker and Mike Shultz formed Cybernance in 2015.
In April, UT McCombs student Charlie Leonard contacted us after finding our Texas CEO article on cybersecurity. He had focused on the cybersecurity industry for two years during his MBA program and had formed a company to address the same problem. When he found us in a Texas CEO article, he reached out to see if we’d talk with him about applying his knowledge and skill set at Cybernance. After only a short time with Charlie, we invited him to become a co-founder!

The Market
It’s critical that we start to demystify cybersecurity for the director community. Directors don’t need to be technology experts, but they must play an effective role in cyber-risk oversight.
Ken Daly, CEO, National Association of Corporate Directors
We found a growing understanding that cybersecurity is more than just a technology problem. The industry standard cybersecurity framework developed by The National Institute of Standards and Technology (NIST), identifies three dimensions of cybersecurity maturity: Risk Management (technologies and processes), Risk Culture (organizational awareness), and Risk Influence (vendors and partners).
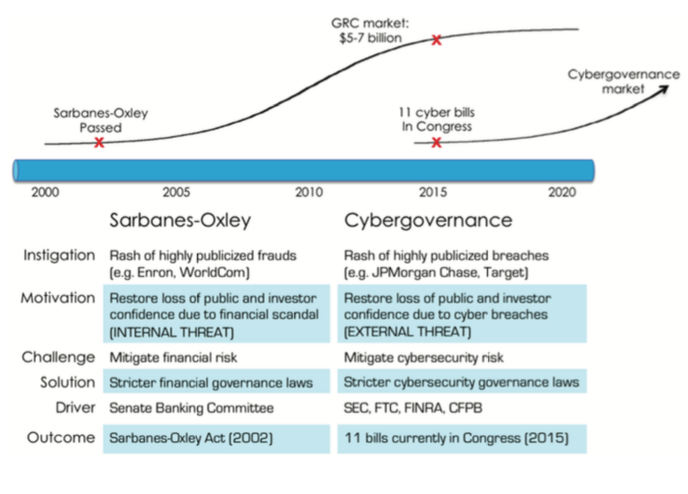
A friend pointed out that cybersecurity governance (aka cybergovernance) is tracking a path similar to financial governance. Highly publicized financial fraud events in the late 1990’s led to the 2002 passage of the Sarbanes-Oxley Act, which regulates compliance with financial operations and reporting standards. The market for supporting products and services grew to $5 billion in 2015 (see diagram below).
The recent tsunami of highly publicized cyber breaches is creating a similar pressure for cybersecurity compliance. Multiple legislative actions, like the Cybersecurity Information Sharing Act passed on October 27, 2015, are in play. Industry experts point toward the likely passage of more legislation in the next 12 to 18 months.
The Solution
We decided to combine a software-as-a-solution (SaaS) platform with legal expense indemnification and accomplish four critical objectives:
- Demystify the highly technical field of cybersecurity for corporate directors. Our software platform establishes a common language for cyber risk that facilitates collaboration between boards, executive management and security experts to mitigate business risk. We built it around our Cybergovernance Maturity Oversight Model (CMOM) that integrates the NIST Framework and C2M2 from the Department of Energy, the two most widely used reference standards.
- Measure a comprehensive set of security controls. CMOM monitors and evaluates over 300 controls across the three dimensions of the NIST Framework and the ten domains identified by C2M2. This comprehensive coverage is presented in simple, intuitive displays that give non-technical directors a deep level of understanding without requiring them to become technical experts.
- Inform the board continually about the maturity of their company’s cybersecurity activities. Since CMOM makes a full range of board-relevant information easily accessible, directors can play an appropriate role in driving organizational change, collaboration, and organizational progress toward cybersecurity maturity.
- Protect the board from personal liability. In the event of a large cybersecurity breach, a board of directors’ worst nightmare is a post-breach shareholder lawsuit exposing them to personal liability. Under CMOM, all their cybersecurity oversight activities are recorded in a repository. In the event of a lawsuit, the repository becomes an essential component of their defense. “Breach of fiduciary duty? No – this board can clearly demonstrate how they exercised prudent oversight over cybersecurity.” In the spirit of “put your money where your mouth is,” we opted to warrant up to $500,000 in personal legal expenses if they employ our system regularly.
Critical Early Tradeoffs
Early in Cybernance’s life, we had long discussions about the potential core business and the many offshoots it could spawn, and all were attractive but potentially distracting. Three high priority tradeoff decisions accelerated the maturation of the company.
1. Marketing Tradeoff: Penetration or Revenue?
In studying adjacent markets as well as the reality and hype around cybersecurity, the enormity of the liability and reputational threats to directors became clear. A year ago, the popular belief was that cybersecurity problems are largely confined to retail, healthcare, and financial services companies because of the types of data they store: personally identifiable information (PII), personal health information (PHI), or payment card industry data (PCI). In reality, almost all businesses are at risk from cybersecurity breaches, e.g., theft of intellectual property from semiconductor companies, access to travel schedules and property layouts from vacation rental companies. Any breach that erodes customer confidence or negates the value of IP can destroy a company.
The lack of a standard model for cybergovernance was hindering the effectiveness of cyber assessments across all types of organizations. Each assessment was a “one off” exercise. We decided to create a common model based on accepted standards that would be easily absorbed and deployed in any organization. And we needed to make it as widely available as possible. While revenue is always a high priority (“cash is king!”), we believed that market penetration was far more important in our specific situation, so we followed that premise in building our growth plan.
2. Development Tradeoff: Time to Market or Low Cost?
A new market doesn’t remain new for long. Getting the Cybernance offering to market rapidly had to be a high priority. The risk from a postponed launch far exceeded our concerns about development cost.
We partnered with a proven software development company to increase the odds that we would meet our objective of creating something universally applicable – very quickly – so we could gain the broad adoption needed to become a de facto standard for cybergovernance. In initial discussions with leadership at our chosen development firm, we reached a mutual consensus that “the cybersecurity market is growing faster than any segment we’ve ever seen” and that the key to success was speed of development and reduced time to market. As a result, our first version was ready far more quickly than it would if we had attempted to build and manage our own development team.
3. Finance Tradeoff: Insurance Model or SaaS Model?
Mike’s original vision for the solution was a hybrid of software and insurance. Together, our team has spent considerable time pondering what a hybrid SaaS/insurance offering should look like. What is the role of each component? How can they complement each other? What is the appropriate pricing model?
The answer gradually crystalized through discussions with hundreds of people: the two components had to be mutually reinforcing. The SaaS solution would excel in identifying and prioritizing risk. With clarity around specific risks, a company would be able to implement risk-mitigating solutions. As those solutions came online, we could monitor the company’s improvements, and use that knowledge as the basis for risk transfer, in the form of insurance. All these actions together improve the cybersecurity maturity of a company, and the insurance provides an incentive for companies to continue focusing on those improvements.
Combining software and insurance into a hybrid solution dictates an insurance pricing model. The cybergovernance console and platform, including the Prudent Oversight Repository, and the legal expense indemnification are provided on a yearly premium basis. Unlike most SaaS offerings with a monthly billing business model that requires significant financial backing to build out the business, our rapid acceptance and market share growth combined with our premium model greatly reduce the volume of investment dollars required.
Each company is unique, so the tradeoff decisions we made may not fit other startups.
How We Work Together
Early on, the founders discussed openly what each of us brought to the table. We agreed to leverage Mike’s strength in financial management and sales, Charlie’s product vision and customer care expertise, and my marketing and partnership knowledge.
Accepting the roles where we had the most talent, and not trying to “group think” every decision, we were able to secure financing and release the product in a matter of a few months. We discuss important matters together, but we take individual action on day-to-day issues with an attitude of “it’s easier to ask forgiveness than permission.”
Results
This will be a marathon, not a sprint. So far the combination of choosing the right market, being deliberate about the tradeoff decisions needed, and developing effective, trusted work relationships is paying off. We achieved our goal of putting the product in the hands of several customers before December 31, and the positive feedback we’ve received since has encouraged us to keep pushing forward.
Dr. Erfan Ibrahim is an early supporter who suggested combining the NIST and C2M2 frameworks. He directs the new Center for Cyber-Physical Systems Security & Resilience R&D at the National Renewable Energy Lab, and he recently commented that “the challenge with cybersecurity is that it is a complex interplay of people, process and technologies whose real value is only apparent when there is a breach. The Cybernance ‘CMOM’ provides a standards based method for evaluating the cybersecurity posture of an organization and easily identifies high priority areas for greater security and reliability. Its software platform offers a powerful tool for my R&D Center at NREL to improve the cybersecurity posture of our clients in the public and private sectors.”